Managed security
Managed Detection & Response (MDR)
Cyberattacks are evolving faster and growing more sophisticated than IT teams can handle alone, increasing risk, cost, and exposure. Traditional security—reacting to alerts—isn’t enough. Our Forrester-recognized MDR combines AI-driven detection with 24x7 SOC monitoring and human-led response to prevent, mitigate, and recover from modern threats—fast.
Get a Free MDR Risk Assessment.png)






The Security Crisis: More Threats, Faster Attacks, Stretched Teams
24B
User names and passwords are found on the dark web
(Source: Darkweb)
$2.7M
The cost of ransomware recovery increased by 78% from 2023 to 2024 (excludes ransom payment)
(Source: The 2024 State of Ransomware Report, Sophos)
60%
of organizations are facing extreme or moderate risk due to security talent shortage
(Source: CyberEdge Group C)
82%
of security teams are overwhelmed by alerts from different tools and lack of a holistic approach to security
(Source: PaloAlto Networks)
Speed, Automation & Human Expertise
The Edge Against Modern Threats
Speed is crucial to outmaneuver today’s stealthy intruders, who can move laterally in as little as two hours. Every second counts when it comes to response - and that's where MDR comes in.
CISOs need assurance that their security program can:
✔ Detect real threats while minimizing false positives
✔ Allocate time and resources efficiently
✔ Reduce Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)
✔ Continuously improve security posture
Our MDR achieves these goals by integrating AI-powered detection, automation, and expert security professionals, working together to help teams detect and respond more effectively.
Why XTIUM?
- 1.7 min MTTD
- 87% faster remediation
- AI + Human SOC Team
- 24x7 SOC + Compliance Expertise
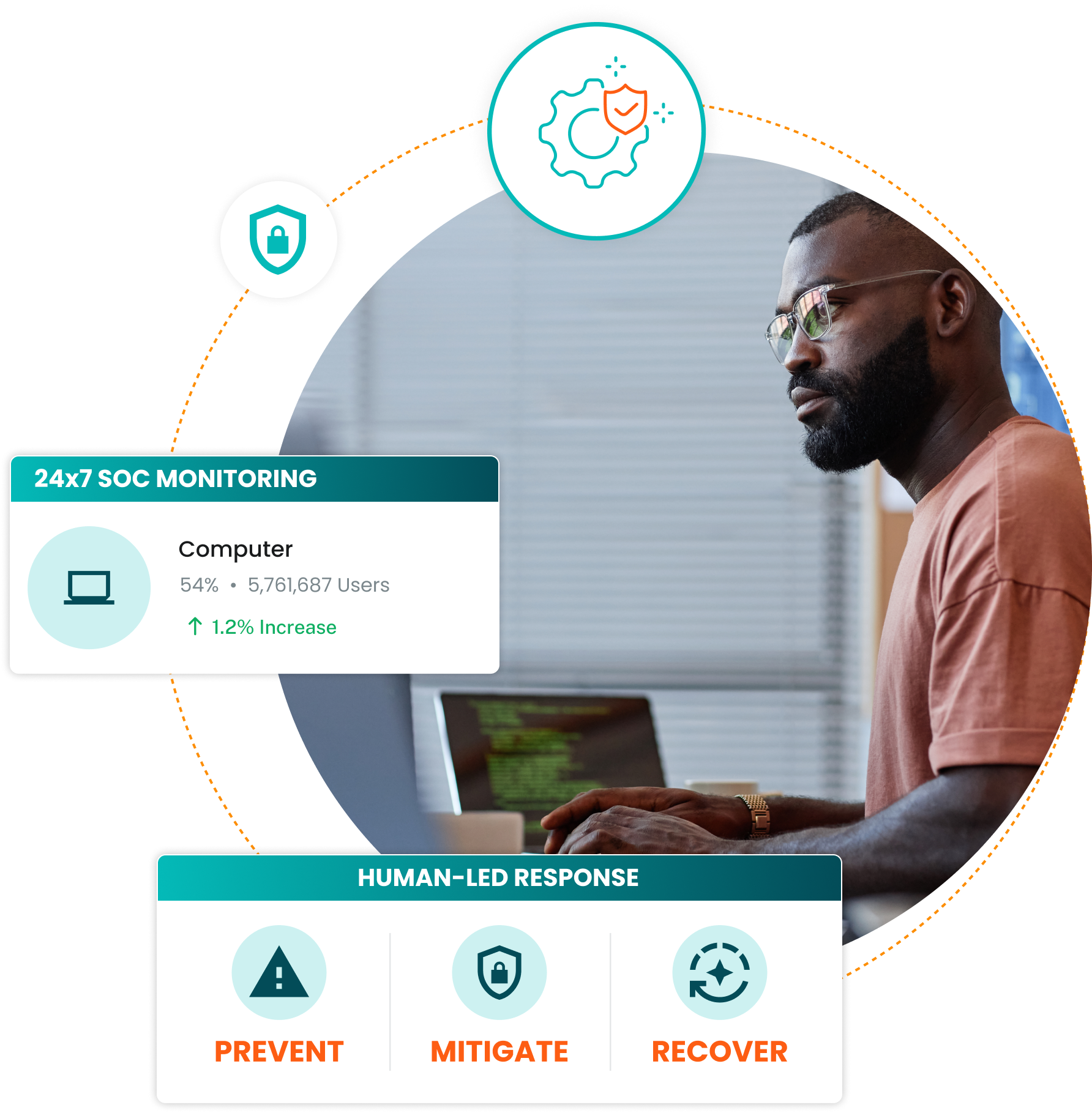
Ready to start the conversation?
People excel where machines don’t, and vice versa — together, they create an optimized approach that responds to threats with precision and speed. Our team will work alongside you from first consultation to daily operations to minimize threats and focus on strategic priorities that matter most.
AI-Powered Approach to Real-Time Threat Detection & Response
Monitor
Respond
Report
Advice
24/7 SOC Monitoring
Get real-time threat detection and response 24/7. Our SOC analysts monitor logs, network traffic, cloud activity, and endpoints in real-time to identify threats.
AI-Driven Threat Detection
We Ingest & analyze vast security data from diverse security platforms, across environments, to eliminate false positives and prioritize real threats—so you can focus on what matters.
Threat Investigation
We investigate threats within minutes and enrich the security alert with contextual insights, helping the team determine attack vectors and threat severity before escalating incidents.
Rapid Incident Response
We respond to security incidents within minutes when a verified threat is detected. Our SOC works with your team to contain, and remediate vulnerabilities before it spreads.
Guidance Remediation & Reporting
We provide quarterly service reports, remediation guidance and recommendations to make informed decisions and ensure threats are effectively neutralized.
SIEM Integration & Metrics
Our platform integrates with SIEM solutions to enhance logging, rule enforcement, and security analytics.
Annual Security Strategy Workshops
Complimentary comprehensive review of your security posture, including a collaborative security roadmap update, ensuring your strategy evolves with emerging threats.
Concierge-Level Security Support
From onboarding to ongoing strategy, we provide a white-glove experience with dedicated cybersecurity advisors who work as an extension of your team.
The Three "R's" of MDR
Legacy security tools, such as firewalls, endpoint protection and SIEM aren’t designed to defend cloud workloads. And automation alone falls short without the right playbook behind it. We go beyond traditional MDR by incorporating the human element and the three essential Rs: Respond, Remediate, and Recover.
-
Respond:
Contain threats in real-time with managed investigation and guided, precise response actions. -
Remediate:
Go beyond detection—receive actionable, step-by-step guidance to eliminate risks and prevent future breaches. -
Recover:
Strengthen your defenses post-incident by implementing tailored rules and workflows to prevent recurrence.
Why Partner with XTIUM for MDR?
Cybersecurity has a speed and efficiency problem. Our Forrester recognized MDR minimizes the gap by blending advanced technology with skilled security professionals, proactively detecting and blocking threats in minutes vs. days to ensure your business stays ahead of attacks.
Proactive Prevention & Detection
1.7 min Mean-Time-To-Detect (MTTD)
Fast Response to Remediation
Improved Efficiency
Extension of your Team
Access to 150+ SOC experts with deep security expertise across industries.
Faster Incident Resolution
51% of organizations see a reduction in Mean Time to Resolution (MTTR) with our expert SOC support
Meet Compliance Requirements
Recognized in the Forrester Wave Report in 2023
Our MDR is built on a leading platform recognized in the Forrester Wave report, ensuring your security posture is always one step ahead of evolving threats.

Healthcare
Cybercriminals target patient records, connected medical devices, and electronic health records (EHRs).
Our MDR service helps:
- Prevent ransomware attacks on hospital networks
- Detect unauthorized access to sensitive patient data
- Ensure compliance with HIPAA and other regulatory frameworks
Finance
Financial institutions are under constant attack from fraudsters, insider threats, and data breaches.
Our MDR service helps:
- Real-time detection of fraudulent transactions and unauthorized access attempts
- Dark web monitoring for stolen banking credentials
- Enhanced PCI-DSS compliance & fraud prevention measures
Retail & E-Commerce
Retailers are high-value targets for supply chain attacks, payment fraud, and credential stuffing.
Our MDR service helps:
- Monitors and protects customer payment data
- Detects compromised employee credentials before they’re exploited
- Safeguards brand reputation by preventing large-scale breaches
Mergers and Acquisitions
Scale your security operations during mergers and acquisitions. XTIUM MDR quickly integrates new environments and security technologies, ensuring immediate visibility and protection—allowing your teams to focus on strategic priorities.
24x7 Global Operations
Ensure around-the-clock protection with continuous security monitoring and rapid incident response. Whether facing threats at 2 AM or during holidays, XTIUM MDR provides immediate expert analysis and action—relieving your internal teams from off-hours coverage.
Alert Complexity and Volume
Turn security alert overload into actionable intelligence. XTIUM MDR’s expert analysts filter out the noise, prioritize critical threats, and provide clear remediation guidance—freeing your IT teams to focus on high-impact initiatives instead of chasing alerts.
Tools to Fill Threat Gaps
In addition to our comprehensive MDR solution, we deliver additional security tools to help businesses fill threat gaps including:
- Endpoint security protection powered by Crowdstrike
- Continuous network vulnerability management powered by Tenable One
- SIEM Event Management, powered by Microsoft Sentinel
The XTIUM Difference
AI-Powered Security & Automation
Because your team can’t afford to manually fight every battle.
Direct Access to Experts
No middle-man, no getting stuck in call queues. You get a direct line to the people that solve problems.
24x7x365 SOC
Always-on protection so you’re never caught off guard.
Predictable Costs, Scalable Support
No more cost overruns or resource shortages.

Ryan Easter

Jeff Francis

Dan Sincavage

Ken Schultz

Chief Information Officer, Friedman, LLP

Charles Halfpenny
Hackers don't break in, they log-in
We deliver multi-factor authentication to prevent breaches, provide secure access to company apps and network from any device on any location, all in a cost-effective and easy-to-implement solution.

Industry-recognized and certified to support your IT needs
Trusted by 1,700+ mid-size and enterprise companies, we operate as an extension of your team—solving problems with urgency and accountability so you can focus on strategy, not firefighting. We are not just another MSP. We're your force multiplier that bring proven frameworks and real-world experience to help you secure, scale and streamline operations with fewer resources. Stop juggling vendors. Stop fighting uphill battles. Work with an IT partner who gets IT.