This isn’t a surface-level scan. Our team of certified experts will deliver a comprehensive, professional-grade assessment including
- Attack Surface Discovery– A visual & tabular breakdown of your exposed assets.
- Vulnerability Scan – Identified risks, categorized by severity & exploitability.
- Security Gap Analysis – Insights into misconfigurations, weak points, and unpatched software.
- Dark Web Exposure Overview – An overview into compromised credentials and leaked sensitive data.
- Critical Risk Summary – A snapshot of the most pressing security threats.
Get Started




A Sneak Peek Into What You'll Get
Obsolete & Unsupported Systems
Critical
Internal Risks
Weak Encryption & Expired Certificates
Dark Web
Exposure
Get Started
Sign Up
Discovery Call
Get Your Results
What’s Included in Your Free Exposure Scan
As part of this limited-time offer, XTIUM will conduct a deep investigation into your organization’s exposure on the dark web and other unindexed online sources – at no cost.
This scan is designed to uncover:
Leaked Credentials
Compromised Accounts
Sensitive Document Leaks
Threat Actor Mentions
Your Dark Web Risk Profile
Threat Intelligence
Access to a real-time threat intelligence feed from over 900 global sources
Plus Threat Intelligence.
As part of the assessment, you will receive a subscription to a curated, real-time feed of cyber threat activity sourced from more than 900 global data points. This will help you stay ahead of emerging risks and get immediate, actionable insight into the threats most relevant to your organization.
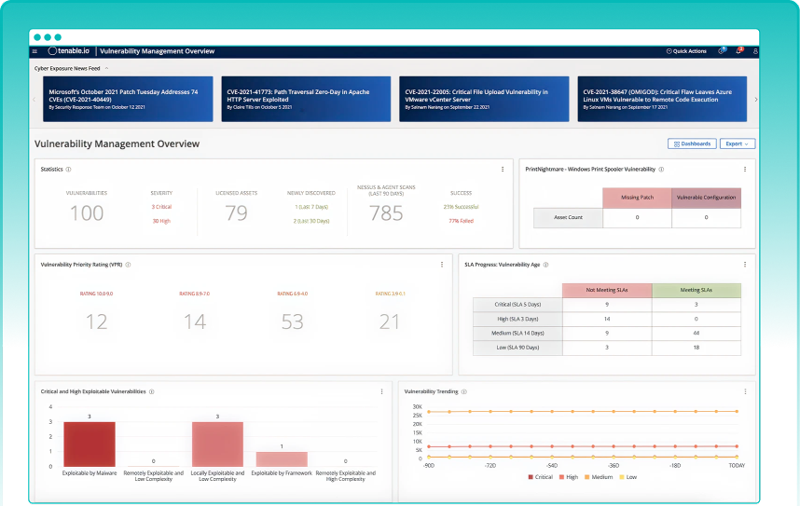
Cyberthreat and vulnerability scanning
It’s not about IF anymore, it’s about WHEN
24 billion
stolen credentials are circulating on the dark web – that we know of. (Dark Reading 2022).
59%
of organizations faced ransomware in 2024, with recovery costs averaging $2.7 million per attack. (Sophos 2024)
$4.88 million
is the average cost of a data breach, making cybersecurity resilience a critical business priority. (IBM 2024)It’s not about fear. It’s about facts.
The XTIUM team of assessment experts will identify:
- If you are already on someone’s radar
- Where your human attack surface is compromised
- What kind of exploitation risk are you carrying
- What can you do about it
We’ll take you from “You’ve got a problem” to “Here’s how you can fix it”

Why XTIUM?
Market-leading Expertise
in both Managed Detection & Response (MDR) and Assessment & AdvisoryAdvanced tooling and expertise
with industry-leading threat, vulnerability, and dark web solutionsDetailed, easy to read reports
tailored to your business, highlighting prioritized risks and next stepsProfessional Services
and certified advisors to support any remediation work you needProactive Threat Detection and Remediation Gives You the Upper Hand.
Industry-recognized and certified to support your IT needs
Trusted by 1,700+ mid-size and enterprise companies, we operate as an extension of your team—solving problems with urgency and accountability so you can focus on strategy, not firefighting. We are not just another MSP. We're your force multiplier that bring proven frameworks and real-world experience to help you secure, scale and streamline operations with fewer resources. Stop juggling vendors. Stop fighting uphill battles. Work with an IT partner who gets IT.